From today, a new authentication level has been added to the sections reserved for administrators, to the existing ones, called “Zero Trust Security”; this particular authentication in the cloud has been activated thanks to the incessant work of our content- [Contents: every content intended as text, images, audio or video] - delivery network- [Network of Contents: is the channel in which owners can post their content and the audience can see the contents posted by the owners] - (also knowing as “CDN” Cloudflare) and consists in receiving a timed PIN via email (or other devices) to be acknowledged at the authentication request. This form of authentication allows us to raise security standards to the highest levels and mitigate unauthorized requests at cloud level.
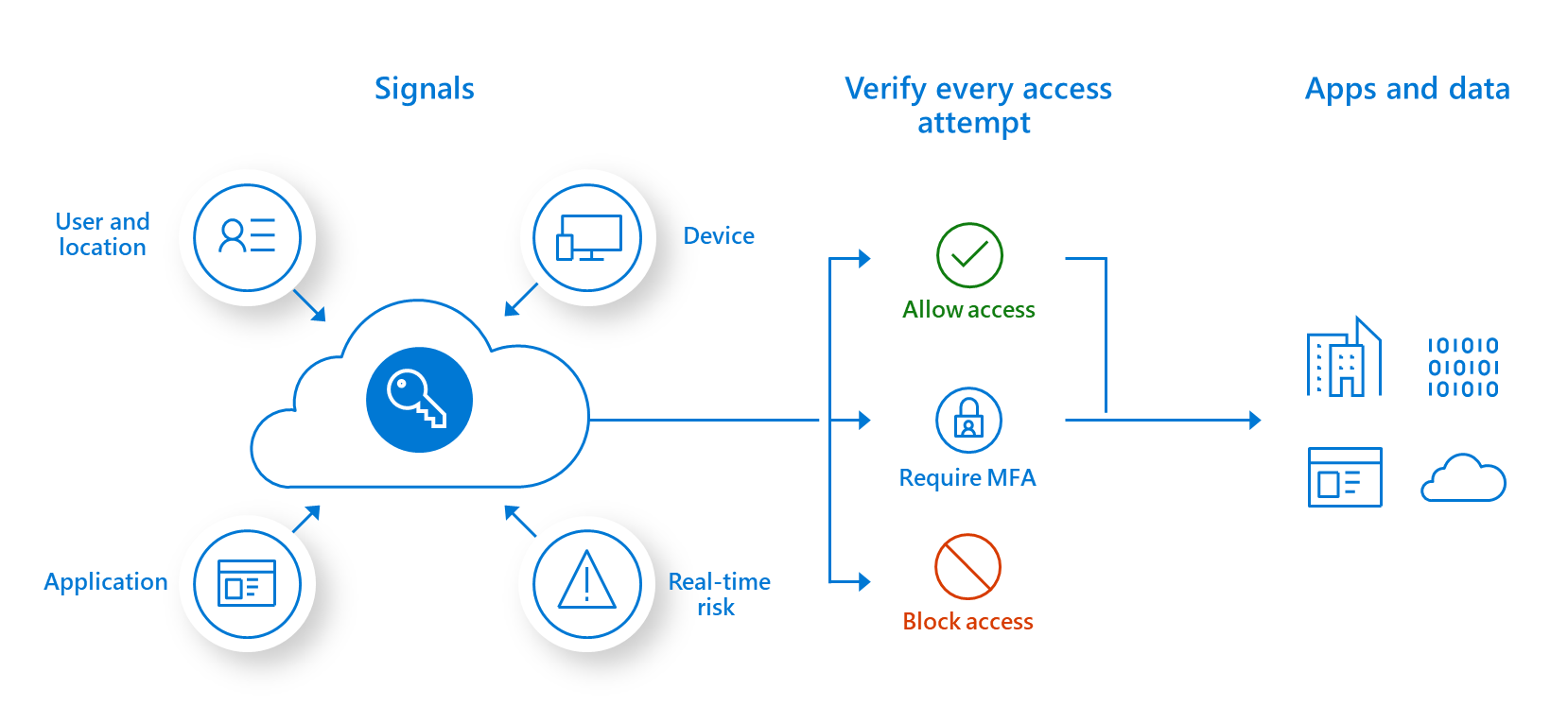
The zero trust security model (also, zero trust architecture, zero trust network architecture, ZTA, ZTNA), sometimes known as perimeterless security, describes an approach to the design and implementation of IT systems. The main concept behind zero trust is “never trust, always verify,” which means that devices should not be trusted by default, even if they are connected to a managed corporate network such as the corporate LAN and even if they were previously verified. In most modern enterprise environments, corporate networks consist of many interconnected segments, cloud-based services and infrastructure, connections to remote and mobile environments, and increasingly connections to non-conventional IT, such as IoT devices. The once traditional approach of trusting devices within a notional corporate perimeter, or devices connected to it via a VPN, makes less sense in such highly diverse and distributed environments. Instead, the zero trust approach advocates mutual authentication, including checking the identity and integrity of devices without respect to location, and providing access- [Access the simple access to a website as a visitor] - to applications and services based on the confidence of device identity and device health in combination with user authentication.
Thanks for reading, folks.

