Today when we talk about data encryption most people think it is normal and simple but it is not always the case; in today’s usage the encryption is used for governmental and commercial purposes but, depending on the country you are in, it is possible that the encryption is not well accepted and it is also possible that the developers have not allowed the encryption of the information they save on their systems (yes that it’s sad but true). We have decided to create these guidelines to shed light on the large and complex encryption work we have created exclusively for MYETV. It is a work carried out and updated over the years and very complex because it takes into account the privacy, data integrity and security of the same; in our terms of service and in the privacy policy there is a point called “ENCRYPTION AND CRYPTOGRAPHY” which explains the techniques used with the relative patents and why they were used. It would be enough to read those two points to understand what we are talking about; in this post we will focus on how encryption on MYETV works. As of today the encryption on MYETV is divided into several parts:
- DNS Over HTTPS (DOH) and DNS Over TLS (DOT): DNS over TLS, or DoT, is a standard for encrypting DNS queries to keep them secure and private at network level. DoT uses the same security protocol, TLS, that HTTPS websites use to encrypt and authenticate communications. DNS over HTTPS, or DoH, is an alternative to DoT. With DoH, DNS queries and responses are encrypted, but they are sent via the HTTP or HTTP/2 protocols instead of directly over UDP. Like DoT, DoH ensures that attackers can’t forge or alter DNS traffic. DOH and DOT are widely used in our datacenters.

- DNSSEC: it helps protect all the platform against cache poisoning and answer forgery at domain level. “DNS Security Extensions,” commonly known as DNSSEC, provide a way to authenticate DNS response data. Before you connect to a website, your browser has to retrieve the IP address of the site using DNS. However, it is possible for an attacker to intercept your DNS queries and provide false information that would cause your browser to connect to a fake website where you could potentially provide personal information (for example, what you think is a bank website). DNSSEC provides a level of additional security where the web browser can check to make sure the DNS information is correct and was not modified. Thus, even if a website is fortified by strong firewalls, an end user’s data and technology will be at risk if a site’s DNS architecture isn’t sufficiently protected with the usage of DNSSEC.
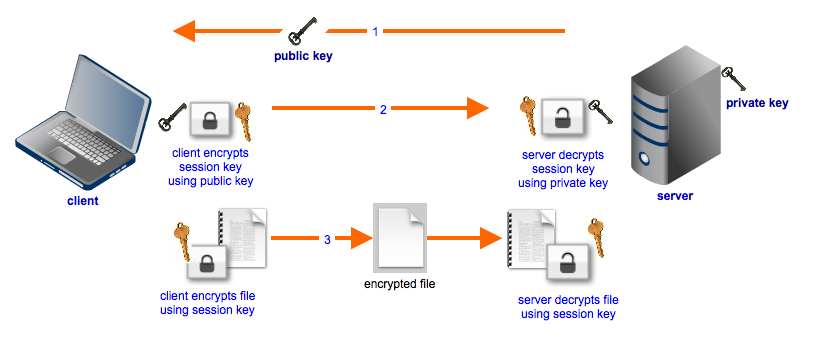
- Encryption in data transmission: this type of encryption takes place at the network level (SSL / https) and guarantees that the information passed cannot be modified or intercepted by anyone else. It is always possible to verify this type of encryption through your browser.
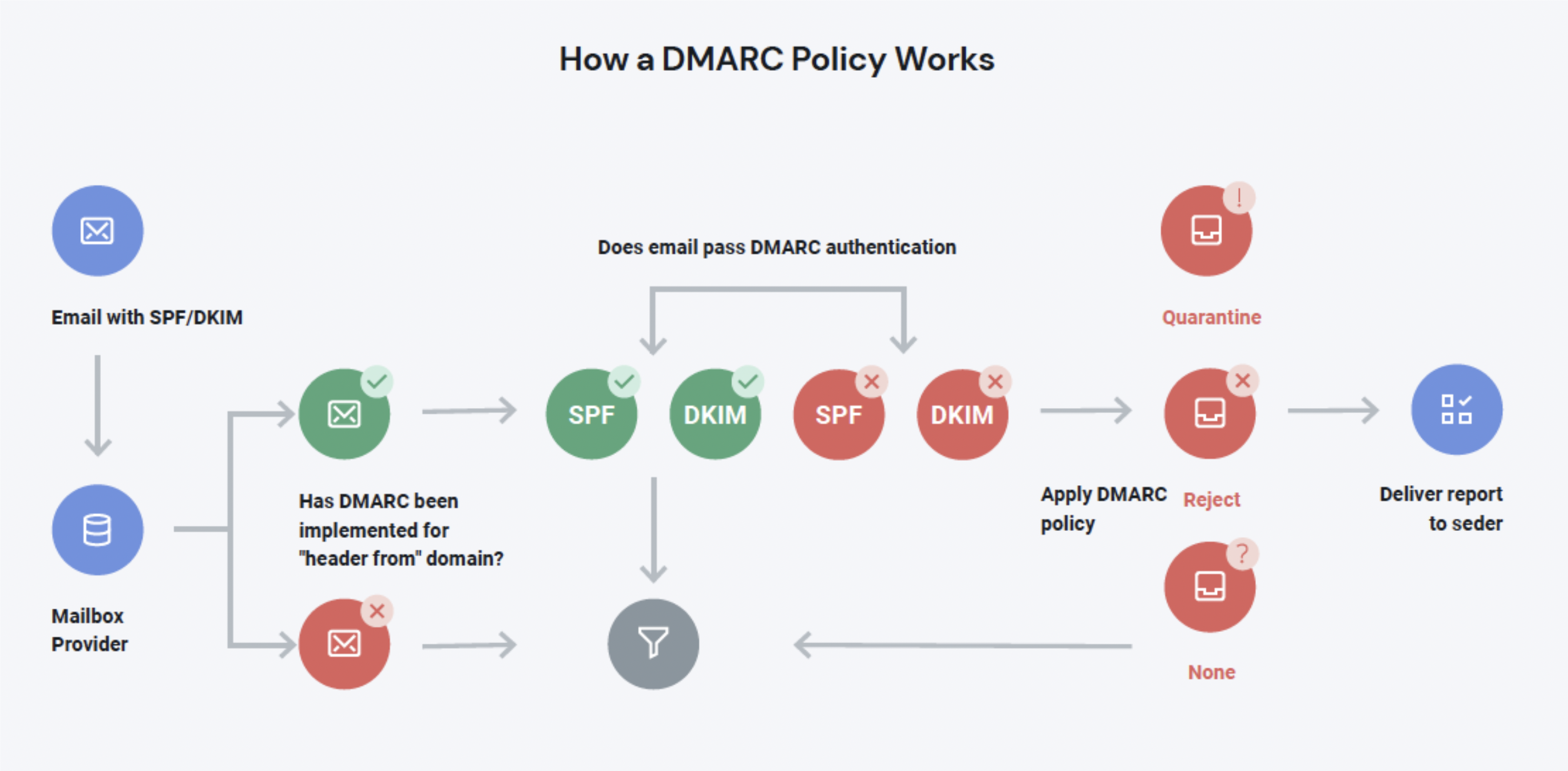
- Email encryption and authentication: messages and updates are an important part of our platform, so our email communications must always be secure and reliable; for this reason the MYETV platform sends emails using a clearly recognizable template and with technology capable of avoiding spam; we use SPF, DKIM and DMARC as authenticatio nand encryption for emails, to have more informations read here: https://blog.myetv.tv/emails-info/
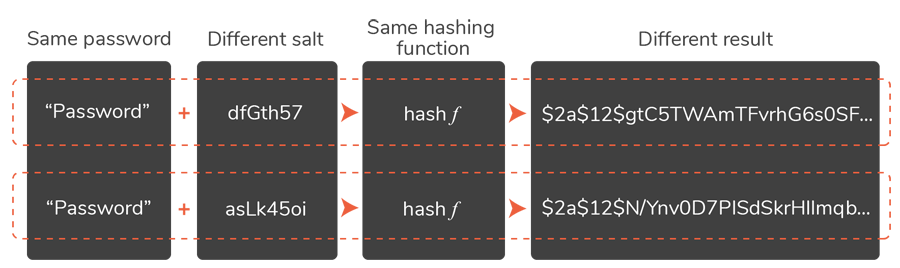
- The encryption on the login information: this type of encryption uses a heavy “one way” hash for the password, which cannot in any case be decrypted, and heavy encryption relating to the username and email (thanks to the AES encryption patent).
- Encryption on entered data (texts): it was also decided to use encryption for all content texts (for example titles and descriptions) and user information (for example name and surname and so on) thanks to the AES encryption and decryption patent; this type of encryption guarantees the integrity of the data, rather than the security of the same.
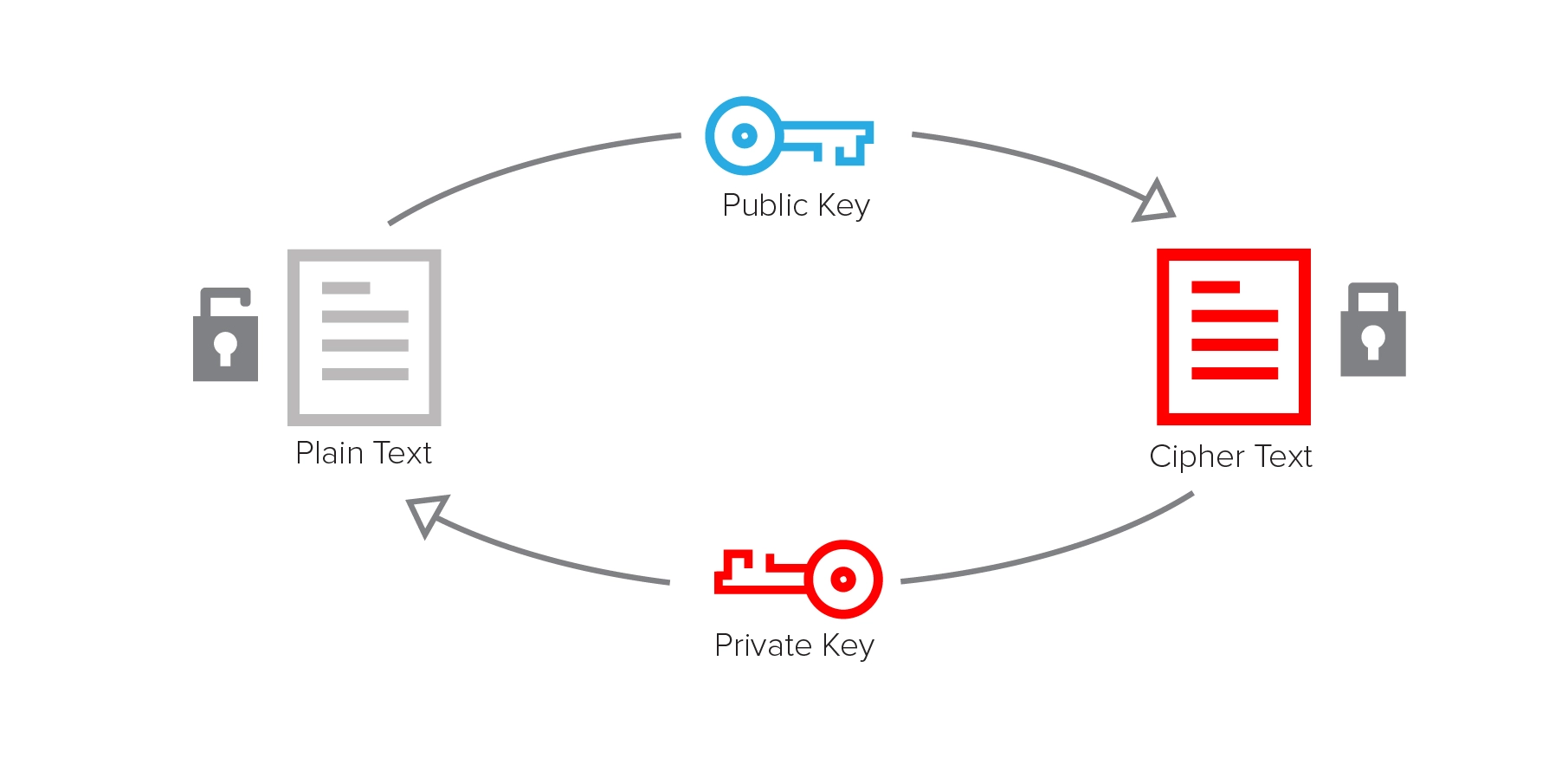
- The encryption used to access information: this type of encryption consists in “tokenizing” some data (for example today’s date and time) and then decrypting them every time a content is requested; this type of encryption is not physical, ie it does not act directly on the saved data, and is usually used to guarantee authentic access to information via HTTP.
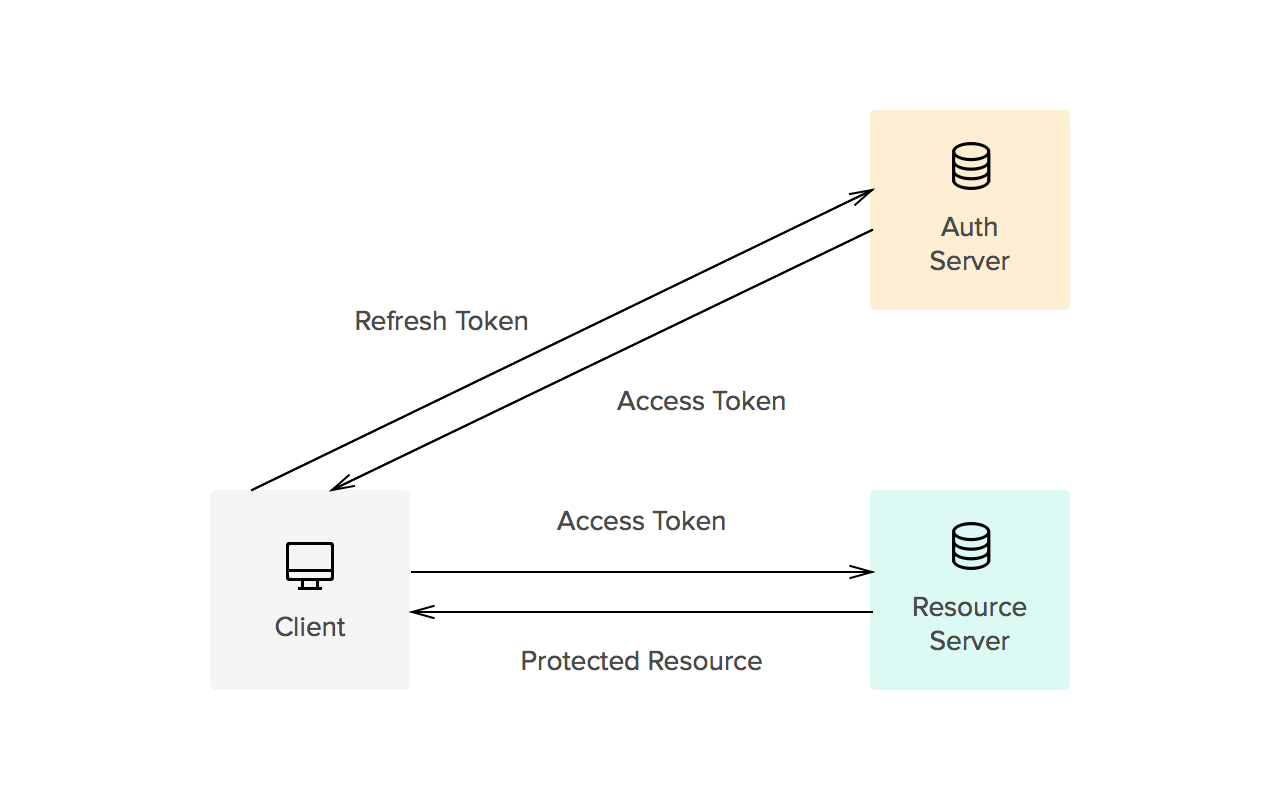
- The encryption of private messages: this type of encryption is similar to that used for texts and allows two people to exchange authentic and secure instant text messages, also guaranteeing the integrity of the information sent.
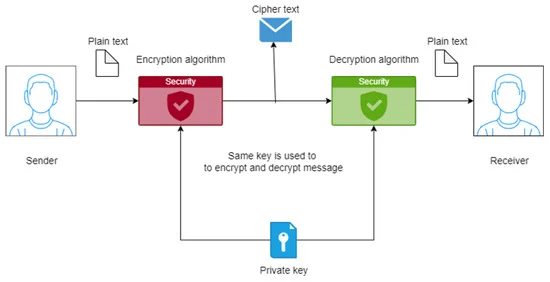
- File encryption: this type of encryption is used in rare cases and only for technical purposes and uses AES encryption patents