In the evening of 10 February 2014 (and later) we have received a really powerful attack. We have defended our website myetv.tv from this attack with all the instruments avaiable; just for understand how big was the attack – 400 gigabits per second – we think that this attack is not started by a single person or even by a small organized collective but it is a targeted attack carried out by an hostile well-organized organization. We have already received a similar attack a few years ago (2008/2009), but this time our firewall and our infrastructure were alerted in time and they immediately sent the logs of what has happened to our American technicians. MyeTV defeated the attack in a few hours, unlike the American engineers who have put a little ‘more time because their infrastructure is very large, we are now back online without losing any data. We really thanks all the people who help on this and we wish to all of you a nice work. We will denounce what happened to the local authorities. An article from rt.com will explain better what happened:
A massive DDoS attack hit EU- and US-based servers, with security companies reporting it to be even more powerful than last year’s Spamhaus attacks. While the method of the attack was not new, CloudFlare warned there are “ugly things to come.”
Only scant details about the attack were released by US-based web performance and security firm CloudFlare, which fought back against the distributed denial of service (DDoS) attack early Tuesday.
According to CloudFlare CEO Matthew Prince, the attack reached 400 gigabits per second in power – some 100Gbps higher than the notorious Spamhaus cyber-assault of March 2013 that at the time was branded the largest-ever attack in the history of the internet.
“[It was] very big. Larger than the Spamhaus attack from last year… Hitting our network- [Network of Contents: is the channel in which owners can post their content and the audience can see the contents posted by the owners] - globally but no big customer impact outside of Europe,” Prince was quoted as saying by TechWeekEurope blog.
Prince said one customer was initially targeted by the attack, but added that he would not disclose the customer’s identity.
The company spent several hours mitigating the attack, but said that the European network was largely unaffected. When helping to deal with the massive cyberwar on Spamhaus last year, CloudFlare claimed it slowed down the entire World Wide Web, which prompted critics to dub the company’s part a “PR stunt effort.”
CloudFlare had some spooky statement to offer its customers this time as well. According to Prince, the latest attack has shown someone has got “a big, new cannon,” and it could be a “start of ugly things to come.”
French hosting firm OVH also reported being hit by an attack of more than 350Gbps in strength, but it was not clear whether it was the same attack CloudFlare experienced.
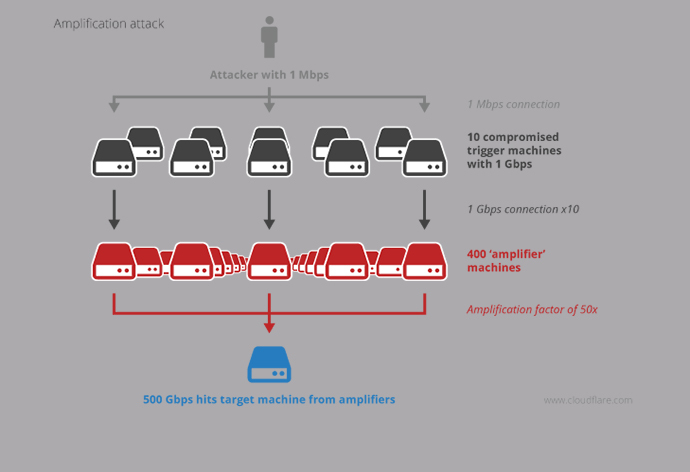
The technique used by Monday’s attackers was not exactly new, as they exploited the Network Time Protocol (NTP) used to synchronize clocks on computer systems. A weakness in the protocol allows querying an NTP server about connected clients and their traffic counts. If made en masse, such requests can generate an overwhelmingly large traffic, bringing down the target just like a typical DDoS attack would do.
What makes the recent attacks worse is the so-called “spoofing” of IP addresses of attackers, making it look as if the victim is actually generating those spam requests. The number of trash requests also skyrockets by “large” replies thrown back at the target from a number of servers “compromised” in the attack. For this reason, such tactics are often referred to as an “reflection and amplification” attack.
Back in January, the US Computer Emergency Readiness Team (US-CERT) issued a warning about such NTP amplification attacks after a number of prominent gaming services were brought down by them in December, including Steam, League of Legends and Battle.net.
While CloudFlare in its warning urged server administrators to patch and upgrade their NTP servers to solve the issue, it appears that few have since bothered to carry out these security measures.
MyeTV is now online and without any problems.
Have a nice day, folks!!!